A Peek Under the [Data] Hood: Finally, ZTNA for Mobile Done Right – And a Checklist to Make Sure
By Will Chow, Mobolize | CTO
If you’re reading this, you’re probably looking for a secure remote access solution for mobile and finding that it is more cryptozoology than cryptography: fast, yet secure, remote access for mobile is practically mythical. Basically, most mobile solutions either use a traditional VPN that exposes your entire intranet to lateral movement, OR use a Cloud Access Security Broker (CASB) or similar web proxy that don’t support all web apps/sites and don’t support mobile apps at all.
 So, it’s no surprise that IT is in the midst of a massive shift towards Zero Trust Network Access (ZTNA), with Gartner projecting 60% of enterprises will have switched over to ZTNA by 2023. However, it turns out ZTNA for mobile is just as elusive as Bigfoot, where most vendors only support desktops, some are simply relabeled CASB products, and many claiming to have ZTNA for mobile are really faking it.
So, it’s no surprise that IT is in the midst of a massive shift towards Zero Trust Network Access (ZTNA), with Gartner projecting 60% of enterprises will have switched over to ZTNA by 2023. However, it turns out ZTNA for mobile is just as elusive as Bigfoot, where most vendors only support desktops, some are simply relabeled CASB products, and many claiming to have ZTNA for mobile are really faking it.
At Mobolize, we have over a decade of expertise in delivering secure, high performance connectivity for mobile devices, including ZTNA, so in this post, we’ll tell you how to tell a real ZTNA mobile solution from a cryptid.
Why is secure remote access so hard for mobile?
The list of challenges for existing mobile remote access solutions is very long, but let’s distill it down to the big ones, starting with those for traditional VPNs. As a reminder, a “traditional” VPN is any that tunnels all of the traffic on the endpoint device into your intranet, such as via IPsec, L2TP and SSL tunnels.
Why traditional VPNs are becoming extinct:
- Sooooo slow: Everything is rerouted through the corporate network, even non-work activity, so this means many more hops that go thru a congested intranet pipe, with the end result being slow internet access, unusable voice/calling apps and escalating IT bandwidth costs.
- No real “splitting”: A traditional VPN can only “split” routes based on IP ranges, so you can’t split by domain or hostname patterns. Since internet IPs are vast and constantly changing, this type of splitting isn’t useful and rarely used.
- No SSO or even MFA: Legacy VPN servers use old-school passwords/keys/certs, which is so insecure that no one should be using them. Very few traditional VPN solutions support 2FA and virtually none have true single sign-on, which all means lower security because of password hell.
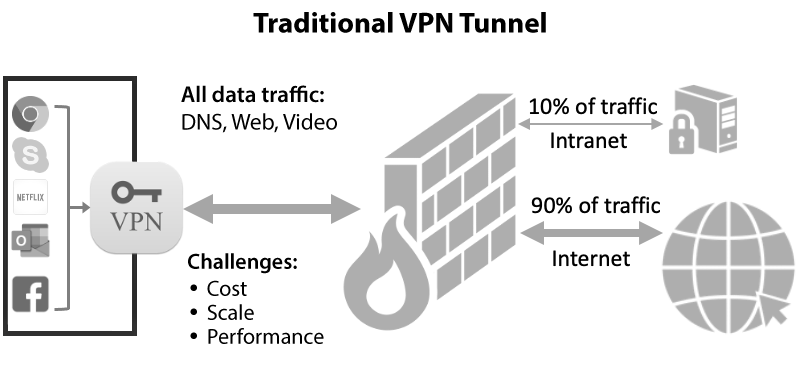
Figure 1 – Traditional VPNs send everything thru your corporate intranet
It’s no wonder enterprise IT is now moving away from traditional VPNs, a technology that’s been largely unchanged since the mid 90s!
Doesn’t CASB solve this problem?
While CASB works great for some use cases, and improves security while simplifying remote access, let’s explore its key limitations, particularly for mobile. As a reminder, a CASB solution operates a web proxy that provides control/monitoring of access to enterprise web apps/sites.
Here’s why CASB doesn’t cut it, especially on mobile:
- URL incompatibility: CASB is billed as “client-less” but must intercept traffic somehow, so they rewrite URLs, which is really hard to get right, fragile and often incompatible with some websites.
- Browser only: You can’t force traffic on a mobile device through a proxy for security reasons (at least not without a client/agent), so that means your enterprise mobile apps are out of luck.
- The bottom 10%: 90% of mobile activity takes place in apps so If your clientless CASB solution is also providing data leak protection (DLP) or threat protection (as is the case for many), being able to protect only 10% leaves a very large blind spot.
CASB has been around for about 10 years, so it’s no surprise there is a new emerging technology known as ZTNA. However, how do you know you’re getting new ZTNA technology versus just a repackaged legacy VPN or relabeled CASB solution?
How do I spot a real mobile ZTNA in the wild?
It’s difficult to know if you have a proper ZTNA solution when it’s hard to see where all the bits in the network are going, and it is even harder on mobile where the OS has the device locked down to prevent any snooping, even if you’re wearing a white hat.
Here at Mobolize, we have lots of experience delivering true next-gen SASE features for mobile such as support for DNS Security, Secure Web Gateway and ZTNA. So, we’ve put together a simple checklist of the key things we deliver in our mobile ZTNA solution that you should look for when you’re hunting for one:
- There is an app for that: A true mobile ZTNA solution can’t just support web apps but must also support mobile apps. And not just apps connecting to cloud services: ask the ZTNA vendor if they support enterprise mobile apps that need to connect to intranet servers seamlessly across both on and off the office network.
- Go full SASE: You can’t mix and match different products/vendors because they will conflict at the network level of the mobile device, so you’ll need a single solution that can provide both access (ZTNA) and protection (SWG, DLP), aka SASE. Often the full SASE feature set is only available for desktop users, so ask them if they provide all the same capabilities on mobile.
- 100% app compatibility: When users spend 90% of their time in apps, it is critical that your mobile SASE solution doesn’t break any mobile apps, otherwise your users just won’t use it or worse, turn it off if BYOD. This is the hard one that most will fail to meet, because there are so many apps (millions) and variables to consider. For example, ask if they can automatically detect and handle apps that do cert pinning.
- Real splitting for the real world: Look for a solution that lets you flexibly control the routing of traffic at an app level. No more tracking IP ranges! For example, ask if they can easily split all Netflix and YouTube servers direct to the internet and do so reliably even if their applicable IPs are vast and frequently changing. And also ask about DNS splitting: can they support DNS lookups to company intranet hostnames while simultaneously supporting LAN hostnames on the home Wi-Fi (e.g. printers, smart speakers, etc)?
- All the single sign-ons: Many will support MFA but not SSO, and not all supporting SSO will support 3rd-party identity providers. A true ZTNA solution will support a variety of identify providers and integrate SSO authentication directly into the traffic handling. For example, ask if their ZTNA solution leverages the SSO login session to directly authenticate the traffic at the packet level (i.e. instead of a separate login for the network layer).
- Good (device) posture: Mobile devices are easily lost/stolen and subject to compromise, so a proper ZTNA solution has the smarts to detect whether the device can still be trusted before it opens the door to your servers. This requires an app, so ask them if they have one. If they say you don’t need one, ask how client-less device posture is even possible (hint: it isn’t).
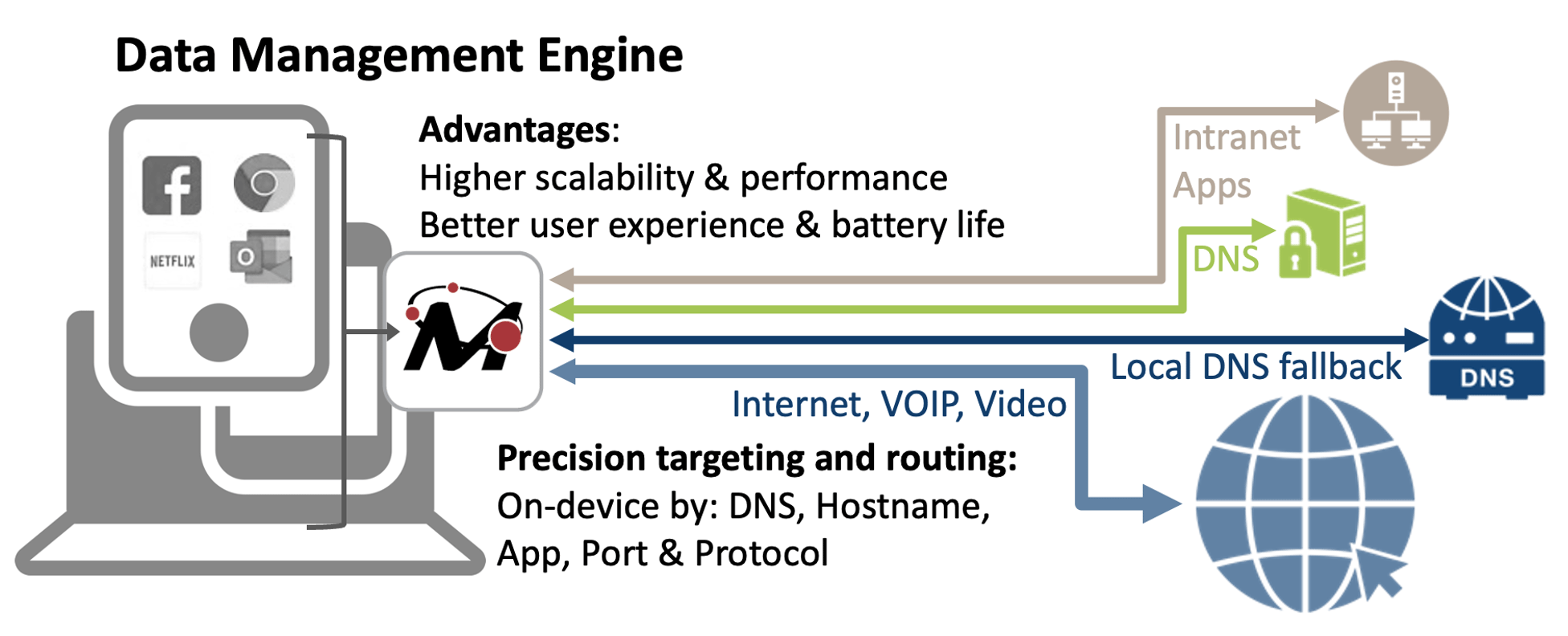
Figure 2 – How Mobolize delivers fast, secure SASE for mobile
There’s a lot more to that list, but those are the big ones to start with. A true mobile ZTNA solution is a rare creature but if you’re looking for one, now you have the key markers to look for that lets you know when you’ve spotted the real deal. Don’t be surprised if you come across vendors that say some of these are impossible, because they are only partially lying: some of these are nearly impossible but absolutely doable with the right expertise. We know, because we’ve done it.




